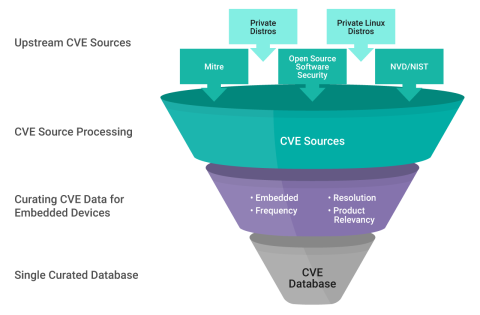
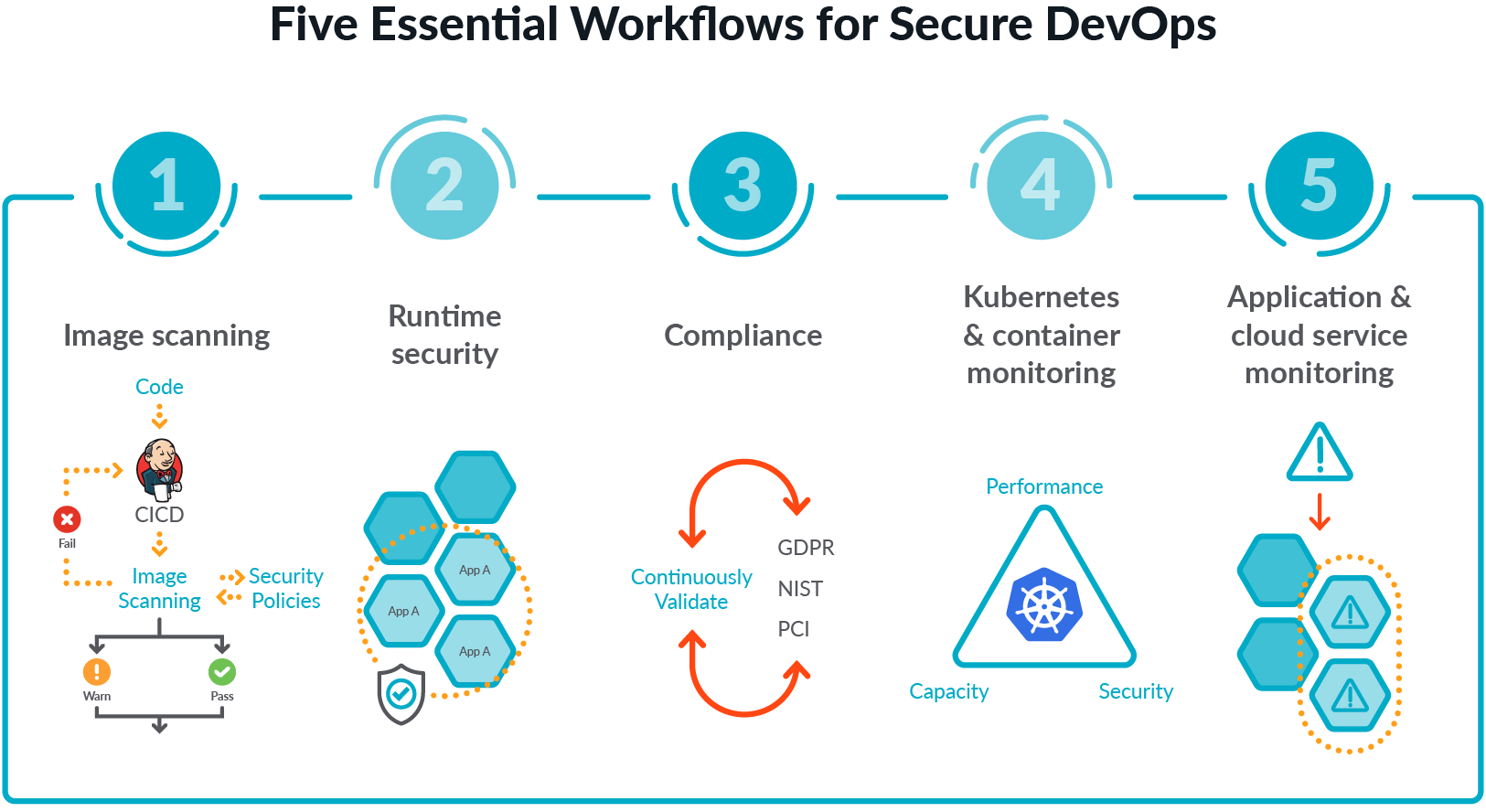
GitHub - vulncheck-oss/cve-2023-36845-scanner: A tool to discover Juniper firewalls vulnerable to CVE-2023-36845
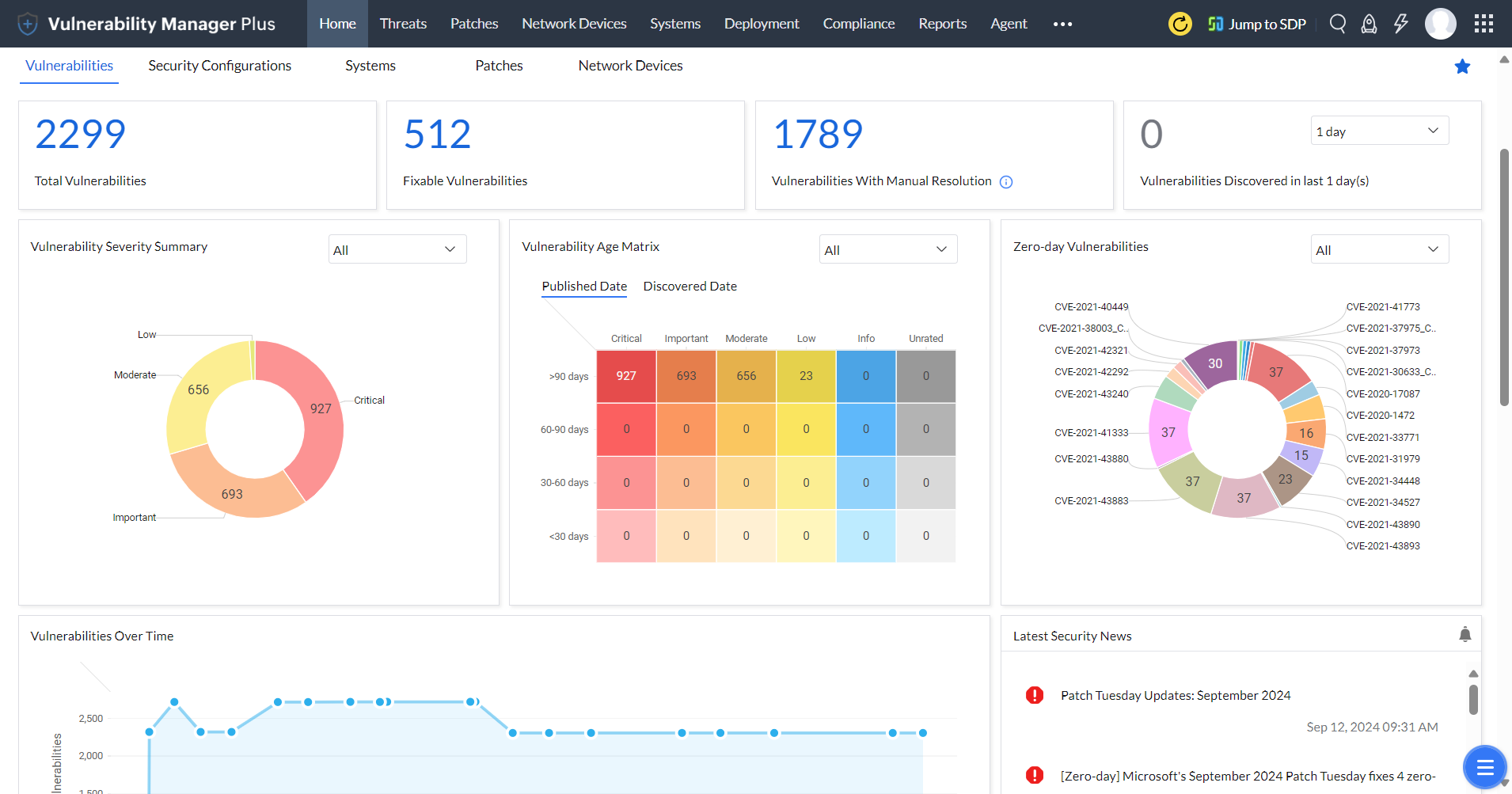
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
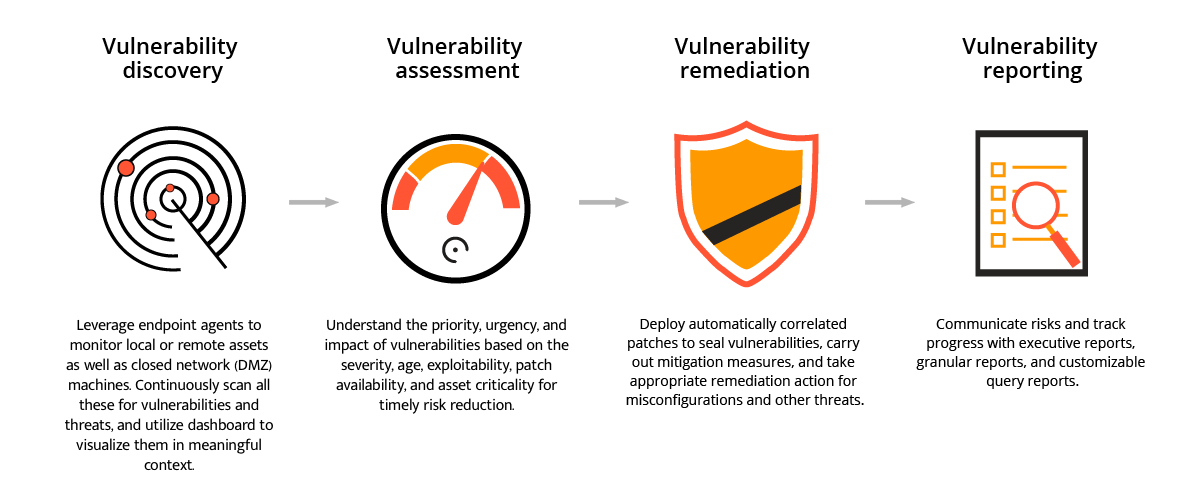
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
![New scanner] Detect vulnerable F5 BIG-IP devices with Pentest-Tools.com | Pentest-Tools.com Blog New scanner] Detect vulnerable F5 BIG-IP devices with Pentest-Tools.com | Pentest-Tools.com Blog](https://content.pentest-tools.com/assets/content/scanner-detect-f5-big-ip/big-ip-vulnerability-scanner-pentest-tools.com_.png)